Information Security
- Introduction
Cyber Defense Exercise Platform (CDX) is to provide an environment for exercise of information security courses offered in coordination with the government's promotion of information security talent cultivation. The platform can be used for long periods of time in coordination with school courses, including the simulation of a real company's network environment with randomly selected vulnerabilities in cyber defense contests, which enhance the hacker defense skills of different sectors.
- Scientific Breakthrough
- Provides an execution environment for information security courses, and simulates the real enterprises network environment for practice, which is accessible at any time of the day by simply connecting to the platform.
- As of the second half of 2017, the platform had been used by 100 academic research units, over 2,500 users, and provided over 150 on-demand vulnerabilities divided into at least 12 categories of information security technology.
- CDX environment deployment only takes 90 seconds to complete, and CDX can create an exclusive isolated environment for information security researchers. Over 15 million samples of malware are provided to academic research units free of charge.
- Industry Applications
The CDX platform uses cloud technologies to provide rapid course environment deployment services, and supports demonstrations and contests held by information security communities at each school. The platform provides an environment for practical talent cultivation and creates an environment that is closest to the workplace of information security personnel, reducing the education employment gap. It can also be used for educational training and information security training in industries.
Cyber Defense Exercise Platform(Open in a new window)
Contact Person:Mr. Lee
Technical support:Mr. Chen
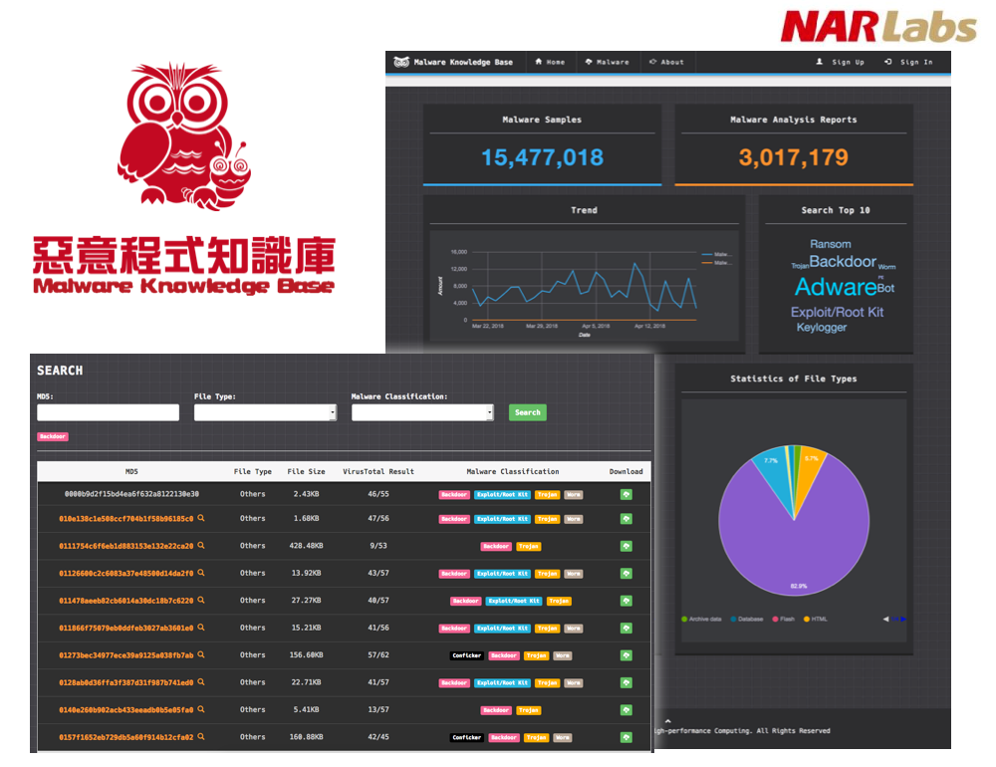
- Introduction
Malware Knowledge Base simulates system and application vulnerabilities and then monitors the cyber-attacks and the corresponding traffic flow. The NCHC established an automated analysis platform for malwares and provides standardized analysis reports for malware behaviors. It deployed a honeynet with over 6,000 IPs on Taiwan's academic network to collect malwares.
- Scientific Breakthrough
- NoSQL database technology is used to accelerate data inquiry and system response, and horizontal expansion can be made in coordination with data growth.
- Malware classification searching and filtering functions are built in Malware Knowledge Base to help users find the malware samples quickly.
- Industry Applications
Malware samples can be provided to the information security industry for research, to validate malware detection mechanisms, and to develop patches and solutions. The list of malicious domains obtained from malware samples can be provided to threat intelligence sharing platforms and strengthen joint defense in the region.
Malware Knowledge Base
Malware Knowledge Base Website(Open in a new window)
Contact Person:Mr. Lee
Technical support:Mr. Ye
 National Center for High-performance Computing
National Center for High-performance Computing